Scanner is a SIEM that is designed from the ground up for cloud scale. It analyzes your logs in S3 cloud storage in-place, and using a novel indexing system, it provides your team with lightning fast search for threat hunting and detections. Ingest terabytes of logs per day at low cost.
Since Scanner is designed for cloud storage and serverless compute, log ingestion is 80-90% less expensive than other tools. You are no longer forced to choose which log sources to drop and which to keep. You can cover them all.
Scanner uses serverless functions to traverse the index files at high speed, allowing users to explore their logs and generate visualizations rapidly. A needle-in-haystack search across 100 terabytes of logs takes less than 10 seconds; across 1 petabyte of logs, less than 100 seconds.
In other tools, high-volume cloud log sources like AWS CloudTrail tend to be discarded due to high cost and slow search speed. This can cause teams to miss attacks like sensitive data exfiltration from S3 buckets, backdoor creation via malicious access keys, and privilege escalation via IAM role assumption. By using Scanner, you can stop missing threats due to lack of coverage on your log sources.
For teams getting started with security, Scanner offers out-of-the-box detection rules for common security logs, like AWS CloudTrail, Cloudflare, Okta, and more. Cover the MITRE ATT&CK framework, or build your own detections.
Build detections with full lifecycles: from alerting to investigation to response. Send alerts to Slack or to SOARs via webhooks, and link alerts to Jupyter notebooks for powerful investigations.
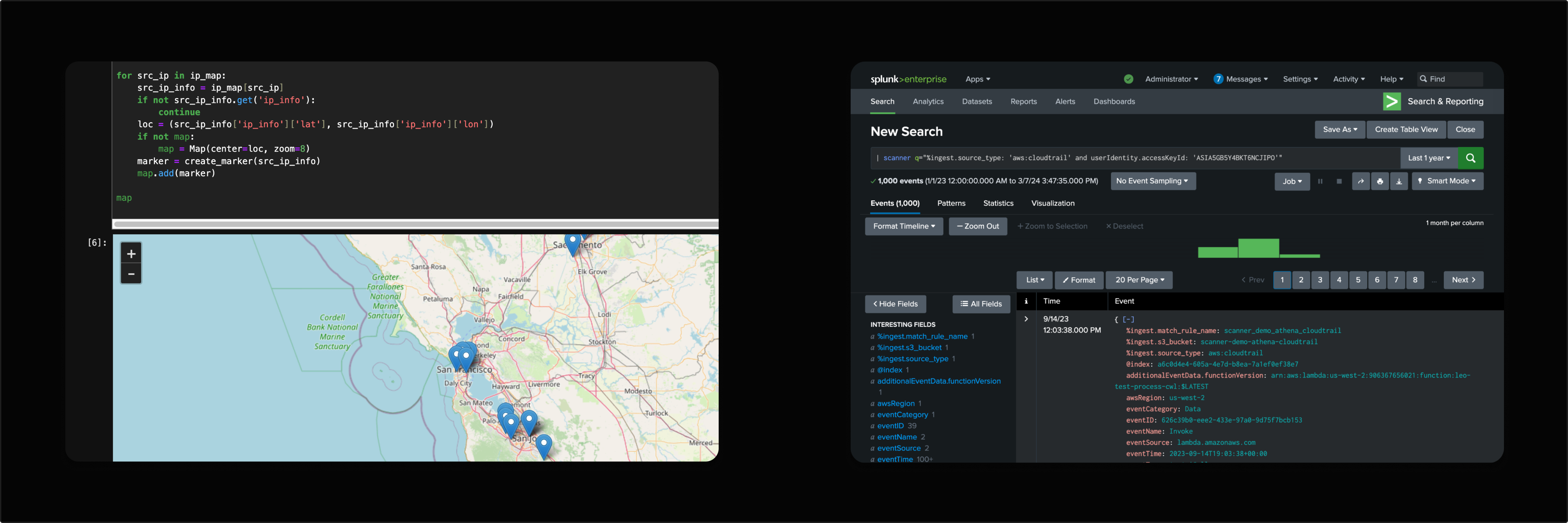
Use Jupyter notebooks built in to Scanner to perform advanced threat hunting and incident response. Write Python code to analyze your logs, create powerful visualizations alongside your response instructions, and share your notebooks with your team for advanced investigations.
For teams that prefer Splunk, Scanner offers a Splunk app that allows you to search your Scanner indexes from Splunk, with custom security content for common cloud log sources, like AWS CloudTrail.

