The Security Data Layer for the Era of Agents
Visibility across all your logs—not just what fits in a SIEM. Search and detect across petabytes in seconds, directly in your object storage. Built for AI agents and modern security teams







































Traditional tools can’t handle cloud scale
Teams are stuck choosing between two broken approaches:
Traditional SIEMs
High ingestion and indexing costs slash retention and force sampling, creating dangerous blind spots.
Endless cluster tuning, shard management, and outages just to keep the system running.
Proprietary formats trap your data, making migration slow, costly, and painful.
Traditional Data Lakes
You must ETL and normalize everything before searching; constantly breaking when schemas change.
Full-text searches can take hours and cost hundreds per run, making investigation prohibitive.
Scheduled queries re-scan data inefficiently, limiting detection to hours or days, never real time.
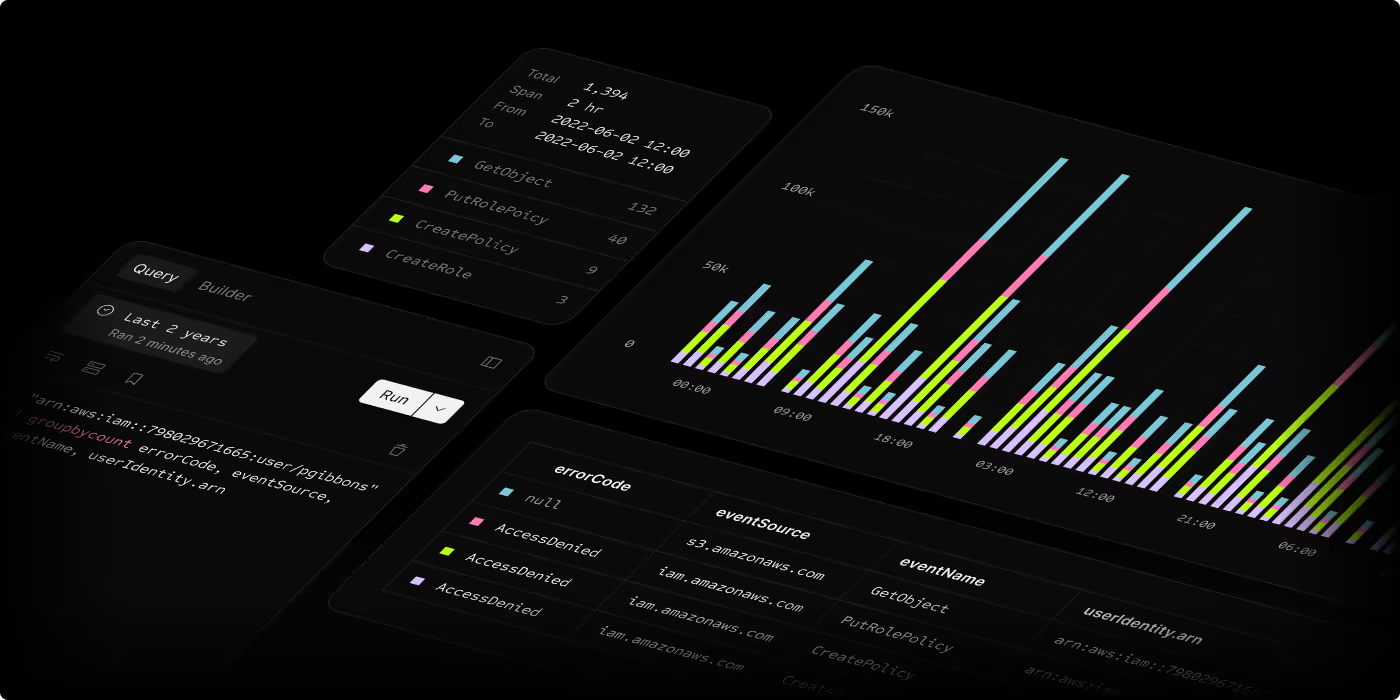
Scanner unlocks the power of your security data
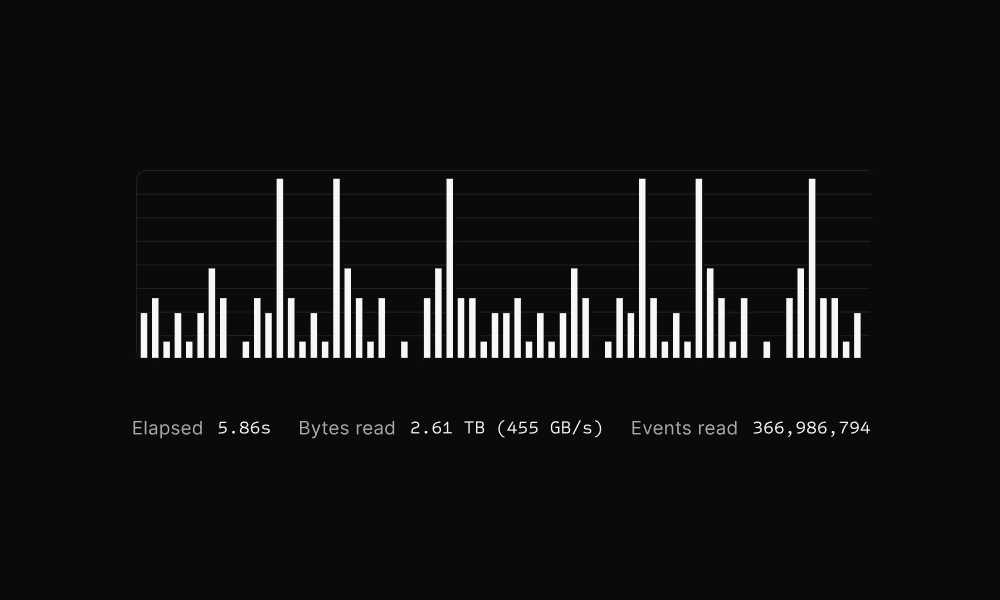
A cloud-native security data lake that never slows down, never drops data, and gives you complete control.
Built for the AI Security Era
Traditional SIEMs can't handle AI workloads. Queries are too slow and too expensive for AI agents to explore freely.
Scanner is the only platform with the speed and economics to make AI-driven security viable.

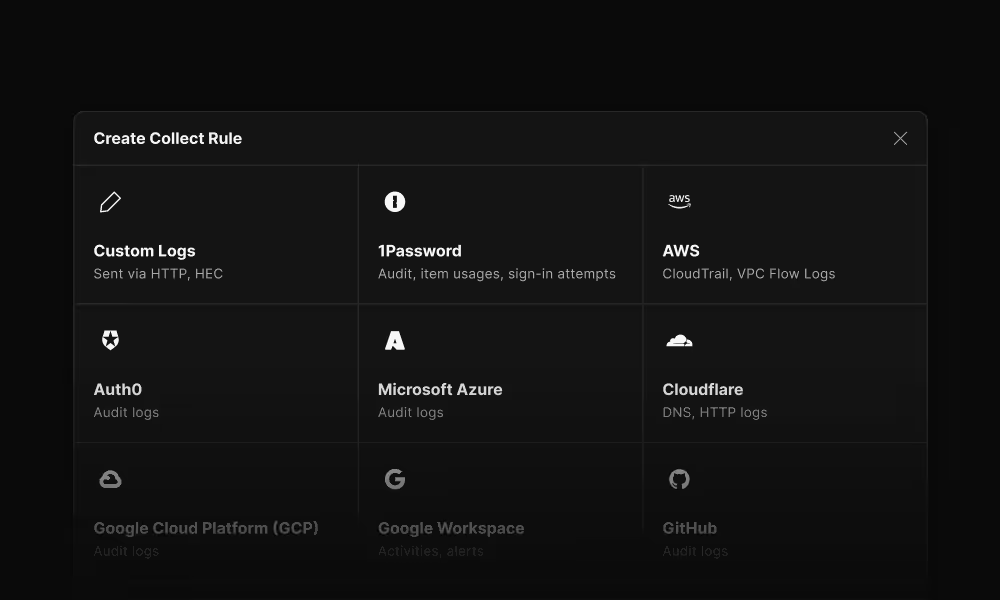
Every query, every dataset available programmatically
Built for integrations, automation, and custom workflows. Connect Scanner to your existing tools and security stack.
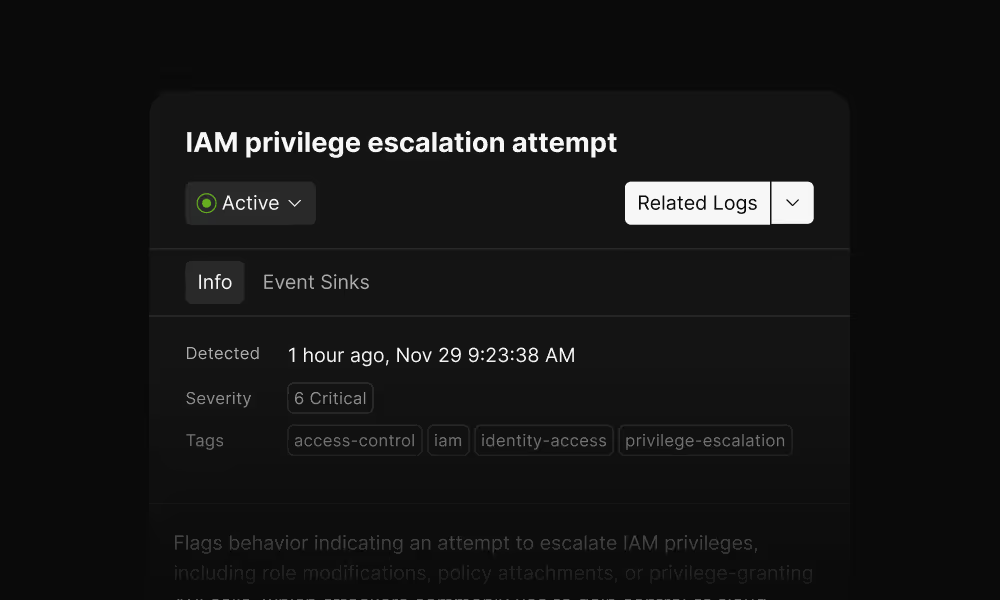
Fast access to your Security Data Lake with Model Context Protocol
AI agents get structured access to your security data through a standardized interface built for intelligence tools.
Fast and economical
for AI to freely iterate
Enable investigations that would timeout or cost too much in traditional SIEMs. AI needs complete context, Scanner delivers it.
“We can search through a full year of logs in seconds, giving us visibility into an order of magnitude more data than before. Analysis at this kind of scale is essential in the cloud era.”
Enterprise-Grade Security
Your data stays in your cloud.
Full custody. No vendor lock-in.
Ready to Transform Your Security Data?
See how Scanner can help you retain everything, search instantly, and unlock AI-powered security workflows.