The Future of Detection: Where AI and Security Operations Intersect

AI is no longer just a buzzword in cybersecurity, it’s becoming a practical, powerful tool for making detection faster, more scalable, and (dare we say) a little less painful.
Security teams are using AI to accelerate log analysis, draft detection rules, and lighten the cognitive load that comes with sifting through mountains of alerts. While we’re not handing over the SOC keys to an algorithm anytime soon, AI is already proving itself as a valuable tool for security engineers.
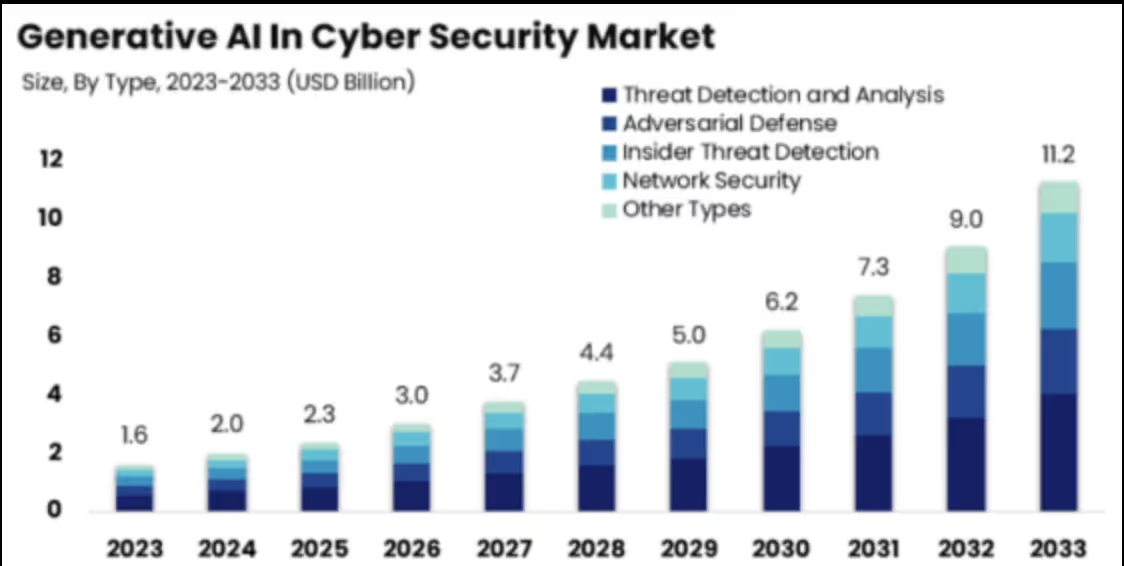
A Growing Market Meets Growing Pressure
The cybersecurity threat landscape is escalating, and the role of AI is growing right along with it. According to MarketsandMarkets, the global market for AI in cybersecurity is expected to nearly triple, from $22.4 billion in 2023 to $60.6 billion by 2028.
Meanwhile, threat actors are already taking advantage. Amazon recently revealed it’s now defending against nearly 1 billion cyberattack attempts per day, up from just 100 million earlier in the year, largely due to AI-powered attack tools.
“Generative AI has provided access to those who previously didn’t have software-development engineers to do these things. Now, it’s more ubiquitous, such that normal humans can do things they couldn’t do before because they just ask the computer to do that for them.”— CJ Moses, Chief Information Security Officer, Amazon.
Where AI Is Delivering Real Value
While fully autonomous SOCs are still an emerging concept, AI is already playing a valuable role in operational workflows. It’s particularly effective at speeding up repetitive tasks and bringing structure to early-stage threat analysis.
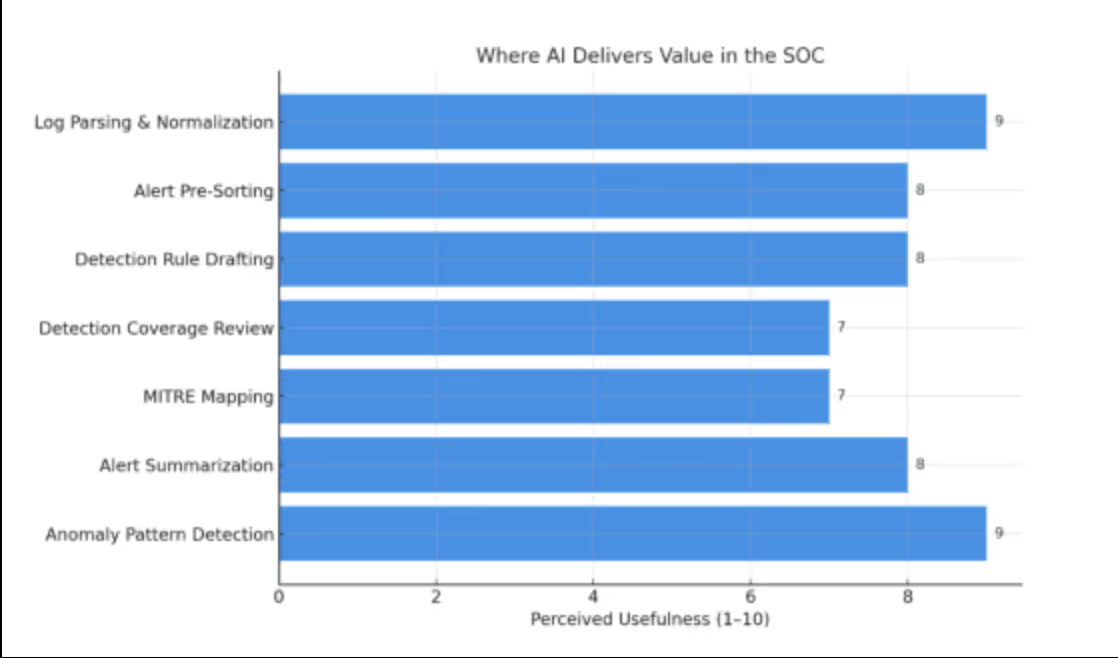
Automating Repetitive Tasks: Security engineers spend countless hours managing logs, tuning detection rules, and responding to low-signal alerts. AI is helping by:
- Parsing unfamiliar log formats and generating draft normalizers
- Pre-sorting alerts by priority and context, reducing triage fatigue
- Drafting detection logic from prompts or examples (bonus: with inline comments and test cases)
According to Prophet Security, AI is most valuable when used to accelerate “low-complexity, high-volume” tasks that take up analyst time.
Brainstorming and Auditing Detection Coverage: AI isn’t just a log parser, it can help analysts think better by:
- Reviewing existing detection sets to surface gaps and redundancies
- Suggesting new rules based on threat intel or under-monitored tactics
- Mapping detection coverage against frameworks like MITRE ATT&CK
These brainstorming and coverage critique capabilities are already being incorporated into advanced AI-driven security platforms focused on threat detection and response.
Reducing Analyst Burnout: Burnout is a real problem in security teams. SOCs are overloaded, and high turnover leads to lost knowledge and increased risk. That’s where AI can help elevate this problem by:
- Summarizing alert context across multiple log sources
- Detecting patterns in high-volume telemetry
- Flagging anomalies that humans might overlook under pressure
The military is using AI to reduce “cognitive load” for analysts and commanders, by using machine learning models to sift through sensor data, generate threat summaries, and highlight priority alerts, AI enables faster, more informed decision-making in high-stakes environments. Tools developed for battlefield intelligence are now influencing commercial security platforms, demonstrating AI’s potential to improve situational awareness and reduce fatigue in complex operational settings.
The Gaps AI Can’t Fill
Despite these wins, AI is far from perfect. There are still major gaps where human analysts are irreplaceable:
Lack of Contextual Understanding: AI can’t distinguish between a threat and a poorly timed VPN login from your CFO. It lacks business context and that’s where false positives still creep in.
Evasion and Novelty: Adversaries adapt. Models trained on yesterday’s threats can be bypassed by today’s variations. Kevin Mandia (founder of Mandiant) warned that AI-powered attacks will soon be indistinguishable from real user behavior.
Data Drift and Model Decay: Log formats evolve. Pipelines break. Threat behavior shifts. Without constant monitoring, models can decay, quietly reducing detection quality until it’s too late.
Best Practices for CISOs
Adopting AI in the SOC is exciting, but also dangerous if rushed or misunderstood. Some key watchouts:
- Over-reliance on automation: AI should support analysts, not replace them.
- Black-box logic: If your vendor can’t explain how alerts are triggered, trust will erode fast.
- Regulatory landmines: Feeding PII into public LLMs could bring compliance violations.
If you’re evaluating AI-powered detection tools, use this checklist to help you get started:
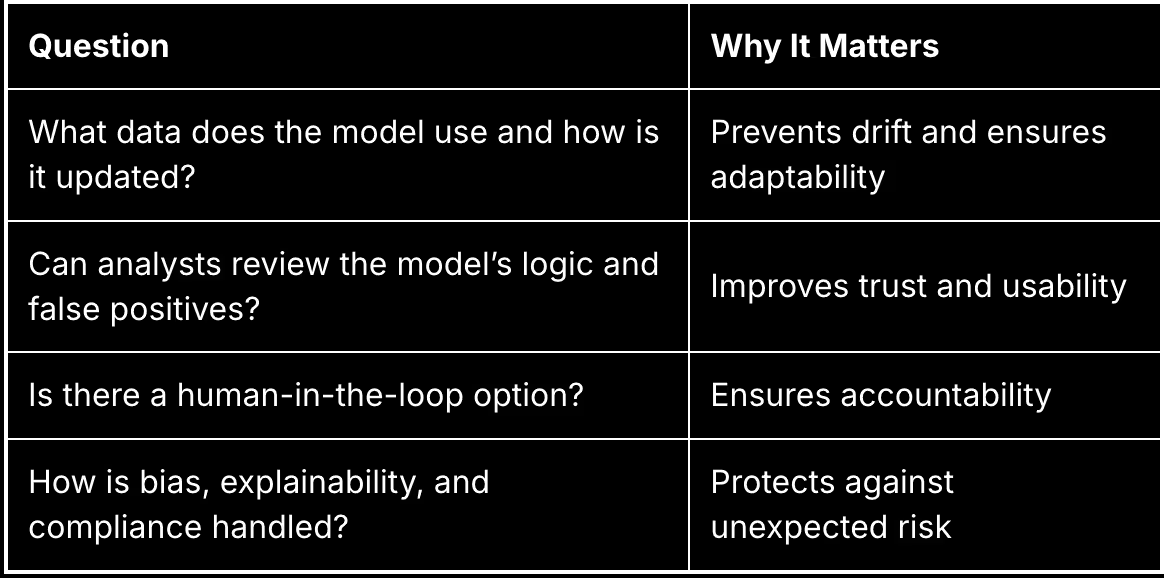
Also, run new AI tools in shadow mode first. Let them learn quietly alongside your existing stack before trusting them in production.
What Humans Still Do Best
No matter how good the model, AI won’t do these alone – yet:
- Hypothesize new attack paths
- Coordinate across teams in an incident
- Customize detections to match your org’s unique business risk
- Build trust with stakeholders during a breach
As OffSec puts it, “The human side of incident response is not just important—it’s essential.”
These aren’t edge cases. They’re the core of what keeps security programs resilient. AI can assist with the mechanics but human analysts still drive the mission. And in high-pressure moments, it’s experience, not automation, that makes the call.
Want Better Security? Don’t Pick a Side—Pair Up
The smartest security programs in 2025 won’t be fully automated or purely manual. They’ll be hybrid, combining the speed and scalability of AI with the judgment, creativity, and context only human analysts can bring.
- AI will reduce noise, generate draft detections, summarize alerts, and help teams stay ahead of known threats.
Humans will apply critical thinking, validate anomalies, respond under pressure, and fine-tune strategy to match business risk. - Together, they’ll power faster, smarter, and more resilient detection workflows.
At Scanner.dev, we’re building toward this future. In the coming months, we’ll be rolling out AI-powered features that help security teams move faster, write better detections, and make sense of messy logs, without replacing the humans doing the real thinking.
Want to stay ahead of the AI surge in SecOps?
Subscribe to our newsletter for updates on how to use AI with Scanner.dev when we roll out our new features.

