Why Fast-Moving Security Teams Rely on Scanner for Detection Alert Analysis
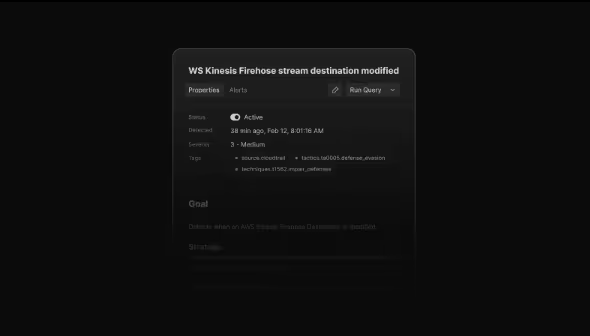
The Detection Analysis Bottleneck
Security teams at modern tech companies are expected to move fast and most importantly stay secure while doing it. As infrastructure scales and complexity increases, alert volume follows suit. It’s not just about alert volume, it’s about how efficiently teams can cut through the noise and act on what matters.
Recent industry reports highlight why alert analysis remains one of the most critical workflows in a security engineer’s day:
- Over 50% of security alerts are ignored due to fatigue and volume. This means actual threats can go undetected simply because teams are too inundated to investigate every lead.
- Security analysts spend 40% of their time manually triaging alerts rather than resolving real incidents . That time could be better used hunting advanced threats or improving detection coverage.
- 76% of IT and security professionals say their SIEM generates too many low-value alerts.
Security teams need speed, not friction. Clarity, not clutter. That’s where a modern, lightweight, and modular alert analysis platform becomes indispensable especially for companies operating at the speed and scale of today’s high-growth tech environments.
The Pain: Why Traditional SIEMs Slow Security Teams Down
Security engineers at high-growth companies consistently express frustration with legacy SIEM tools.
One of the biggest issues is alert noise without context. Most SIEMs collect alerts but do little to enrich them. Engineers spend time digging into logs, cross-referencing with threat intel, and correlating historical data all manually.
“Our SIEM is definitely one of the old-school, traditional SIEMs that is too trigger happy. It produces over 50,000 alerts per day. We basically get an infinite number of these micro-alerts, and there is absolutely no way we could investigate each one.” – Senior Security Engineer, at a Managed SOC team
Another challenge is slow, bloated interfaces. Basic queries can take 1 to 5 minutes in traditional SIEMs, and more advanced queries can take hours to run and cost hundreds of dollars in rehydration costs. During a live incident, that delay could mean an attacker gains further foothold in the environment.
Traditional SIEMs are also known for rigid detection logic. Rules must be manually written, tested, and tuned. It can take weeks before detections are fully operational.
Why this matters:

Every minute wasted on clunky interfaces and manual filtering is a minute attackers move deeper into the system.
The Solution: How Modern Teams Streamline Alert Triage
The security engineering teams behind some of the world’s fastest-growing SaaS companies, teams like those at Ramp, Lemonade, and Postman don’t have time for slow, bloated workflows. They require tools that are fast, modular, and purpose-built for high-speed environments.
What makes these tools different:
- Modular setup: Teams can activate only what they need—whether it’s detection logic, data sources, or enrichment modules. This keeps the interface clean and the workflows fast.
- Real-time summaries: Alerts are automatically enriched with relevant metadata, such as source IP, user identity, asset criticality, and historical context. Analysts see not just what happened, but why it matters.
- Effortless integrations: Modern detection platforms work out of the box with Slack, PagerDuty, Jira, and major SIEM/SOAR platforms. Alerts are routed wherever the team already works, enabling instant triage.
- Blazing-fast performance: Searching for the needle-in-the-haystack takes seconds, even if you have hundreds of terabytes or petabytes of logs.
Performance Comparison
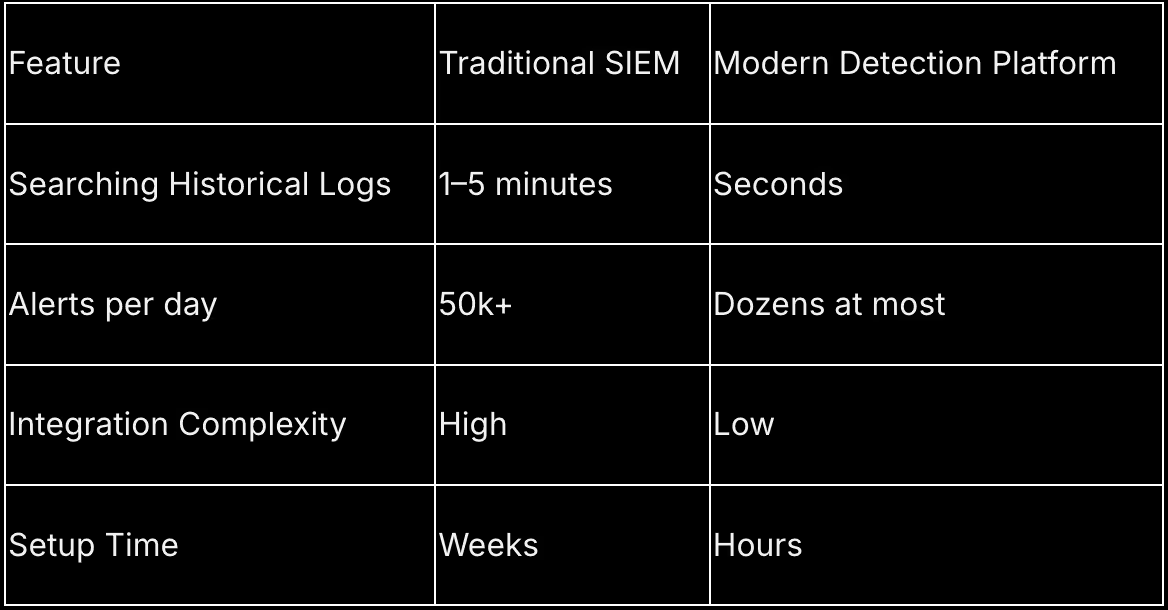
The result means less friction, faster detection, and a workflow that fits the pace of fast-moving teams.
High-Severity Alert in a Next-Gen Detection Workflow
A modern detection pipeline doesn’t just reduce mean time to respond (MTTR), it minimizes risk exposure by delivering enriched, actionable alerts with built-in response mechanisms.
Here’s how a high-severity alert flows through a next-gen platform like Scanner.
- Log Data Ingestion
The platform ingests security log data in real time, whether these logs are cloud provider logs, endpoint telemetry, or third-party security APIs. Ingestion pipelines are decoupled and scalable, ensuring no delays during burst periods. - Powerful Detection Logic
The platform uses expressive detection queries to uncover real threat patterns across your data:- Time-range correlation: Link related activity across hours or days – not just within a single event.
- Cross-log queries: Match indicators or patterns across different sources like Okta, AWS, and endpoint telemetry.
- Chained rules: Detect behaviors like privilege escalation, lateral movement, or suspicious logins – even if they unfold gradually.
- Custom workflows: Write detections as code (YAML + queries), version them in Git, and tune for your environment.
- Smart Routing & Notification
Alerts are prioritized and routed to the appropriate on-call responder via Slack, Microsoft Teams, or integrated alerting tools (e.g., PagerDuty). Alerts include:- Risk score and justification
- Suggested next actions (based on prior IR outcomes)
- Suppression of known benign patterns
- Analyst Triage & Decisioning
Analysts triage in-platform or from chat:- Minimal context-switching—raw log data, enrichment, and prior detections are all accessible
- Guided workflows reduce cognitive load and bias
- Confidence scoring and threat context accelerate prioritization
- Automated or Assisted Response
Analysts can initiate:- Predefined SOAR playbooks (e.g., isolate host, revoke access)
- Escalations to senior IR teams with full context trail
- Post-action logging for compliance and auditability
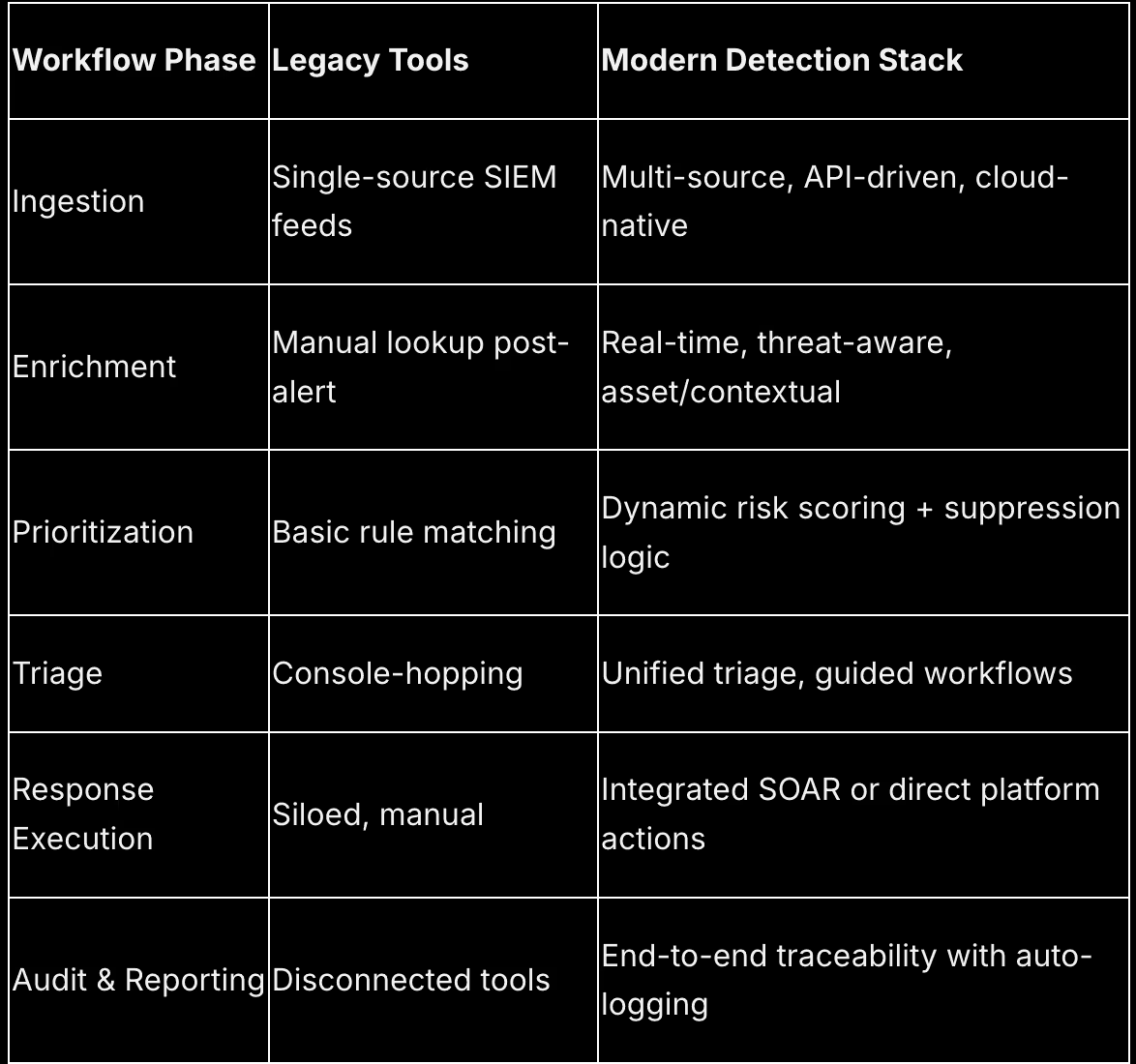
Why It Matters:
CISOs don’t need more alerts, they need fewer, higher-confidence alerts with clear context and swift resolution paths. Modern detection platforms shrink the gap between signal and action, reduce dwell time, and enable lean teams to operate like enterprise-scale SOCs.
Built for Cloud-Native Security
Today’s infrastructure is distributed, fast-moving, and complex. Scanner is built to match it.
- Built for cloud-first teams and modern infrastructure: Scanner helps security teams stay ahead of threats across complex cloud environments and SaaS ecosystems. Whether you’re monitoring AWS, GCP, Azure, or tools like Okta and Duo, Scanner delivers fast, reliable detection and investigation.
- Ingest petabytes, search in seconds: Scanner’s serverless, cloud-native architecture is optimized for scale. It ingests massive volumes of log data and makes it instantly searchable – without the traditional cost or complexity of legacy SIEMs.
- Custom detection, your way: Define detections as code using YAML, manage them in GitHub, or configure them directly in the UI. Scanner’s flexible engine adapts to your team’s workflow – whether you’re automating everything or iterating live.
Modern platforms fit your stack instead of forcing your team to adapt.
Why Speed and Simplicity Matter
The numbers speak for themselves:
- MTTD (Mean Time to Detect) was reduced 50% among teams using advanced detection.
- 83% of analyst report improved workflow efficiency, thanks to fewer false positives and more actionable alerts.
Simpler tools mean more time spent on analysis and response. When security engineers aren’t bogged down by noise, they can actually do the job they were hired for: protecting the company.
Built for the Teams Who Can’t Slow Down
Security teams at high-velocity companies don’t just need more alerts, they need the right alerts, delivered fast, in the places they already work.
The best detection platforms deliver:
- Speed – No delays, no bottlenecks.
- Simplicity – Easy to use, easy to maintain.
- Precision – Alerts that matter, routed in real time.
That’s why forward-thinking teams from product-led startups to scaled enterprises choose Scanner.
Because in environments where every second counts, detection shouldn’t be a drag on your team, it should be your edge.
See how it fits your stack.

