Announcing Scanner MCP: Connect AI Agents to Your Security Data
Today we're announcing Scanner's Model Context Protocol (MCP) server: a remote MCP server that connects AI agents directly to your security data lake. This unlocks a new generation of AI-driven security operations: interactive investigations, AI-assisted detection engineering, and autonomous response workflows.
Why This Matters
Traditional data lake tools available for security operations have a fundamental problem: tools like Athena and Presto weren't designed for AI agents. They're too slow and too expensive for the iterative, exploratory workflow that effective AI agents require.
AI agents need to experiment. They don't know in advance which queries will be useful, so they need to explore freely, refine hypotheses, and follow leads as they emerge. When queries take 30-45 minutes and cost $75-100 each, this iterative approach becomes impractical. By the time results return, investigations timeout. When every query drains your budget and consumes immense time, agents must ration investigation. This is the opposite of what's needed for effective threat detection.
Scanner changes this equation. Using inverted indexes built at ingestion time, Scanner scans only relevant data (2-5 GB instead of 10-15 TB for a typical 6-month query), completing queries in 1-3 seconds for pennies instead of waiting 30+ minutes and spending $100. AI agents can finally work the way they should: exploring every hypothesis, correlating across data sources, and investigating threats without artificial constraints.
What Scanner MCP Enables
Scanner implements Anthropic's Model Context Protocol (MCP), an open standard for connecting AI systems to data sources. This means Scanner works seamlessly with Claude Desktop, Claude Code, Cursor, and the Claude Agent SDK. One integration, multiple tools. As the MCP ecosystem grows, Scanner's connectivity expands automatically.
What makes Scanner's MCP implementation particularly powerful is the combination of protocol standardization with Scanner's performance characteristics. While MCP provides the universal interface, Scanner's indexed query engine delivers results in seconds rather than minutes, enabling the rapid iteration AI agents require. Scanner MCP also implements efficient context management: queries return smart summaries rather than raw data dumps, allowing AI agents to handle large result sets without token bloat that would otherwise limit investigation depth.
With Scanner MCP, security teams are building AI-powered workflows across three core use cases:
1. Interactive Investigations
Interactive investigations put you in the driver's seat while AI handles the heavy lifting. You ask questions in natural language, your AI queries Scanner iteratively, and you refine the investigation direction as findings emerge.
Use Claude Desktop with our MCPB extension for a conversational interface that makes investigating security data as natural as asking questions. This is how humans and AI work best together: combining human intuition and expertise with AI's ability to execute queries, correlate data across heterogeneous log sources, and maintain investigation rigor at scale.
Learn more about Interactive Investigations →
Example: Investigating Unusual S3 Access
You receive an alert about unusual S3 access. Here's how the investigation unfolds:
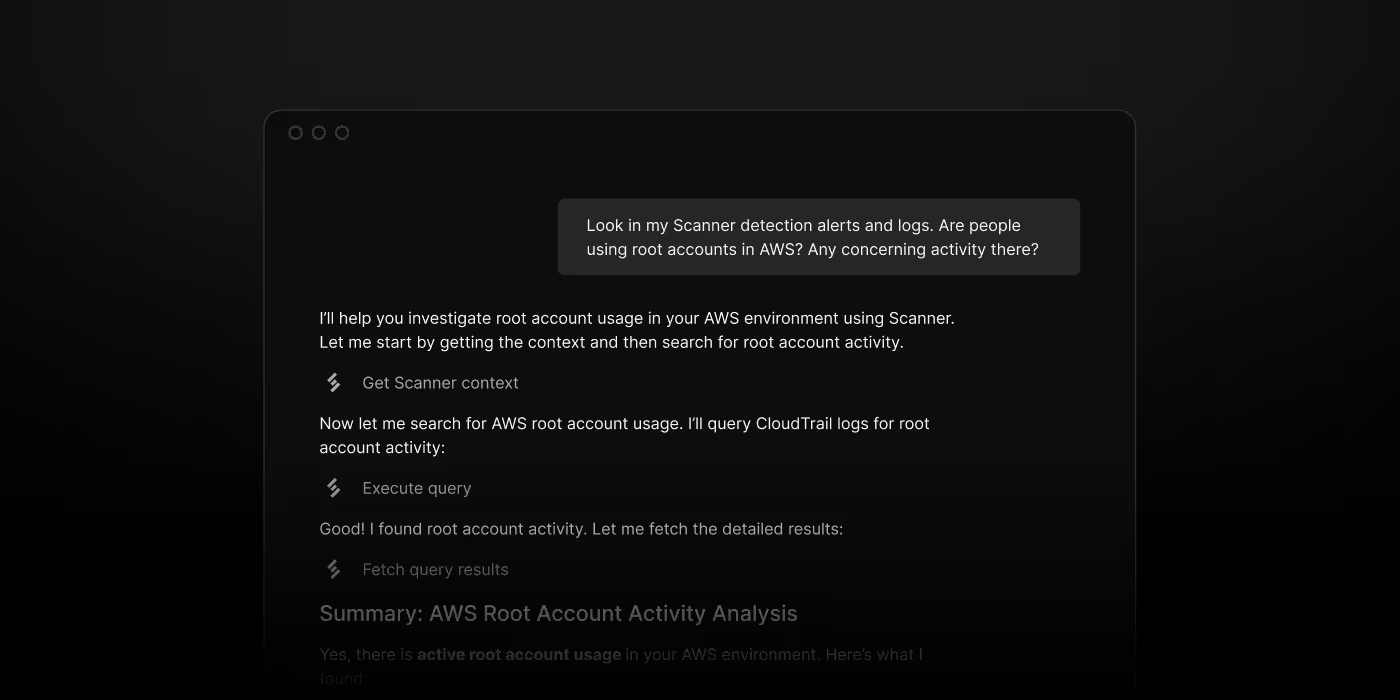
You: "I'm seeing unusual S3 access patterns from john.smith. Can you investigate whether this is legitimate work or potential data exfiltration?"
AI: [Queries Scanner] "john.smith accessed 'sensitive-customer-data' bucket 47 times in the last hour. Highly unusual. They typically access engineering datasets. At 14:23 UTC, they assumed an elevated IAM role (data-access-admin) they don't normally use, then 3 failed GetObject attempts before successful ones."
You: "Check if the account is compromised. Unusual login location?"
AI: [Queries authentication history] "Login looks normal: same IP, corporate VPN. But the elevated role uses temporary credentials expiring in 1 hour. Total transfer: only 2.3 MB (metadata/small files, not bulk download). Recommendation: Flag for review. Could be legitimate security testing, but elevated role usage without a ticket is concerning."
This investigation (which would take 2-3 hours of manual query writing) completes in 5 minutes.
Example: Privilege Escalation Hunt
You want to hunt for privilege escalation attempts:
"Find suspicious IAM policy modifications in our AWS environment over the last 7 days."
Your AI searches CloudTrail logs for failed policy modifications, identifies a user with 23 attempts, analyzes their historical behavior, discovers several attempts succeeded, correlates with authentication anomalies (unusual login location), and delivers a complete attack timeline with MITRE ATT&CK mapping. You don't write a single query.
2. Detection Engineering
Detection engineering with AI transforms how security teams write, test, and validate detection rules. Instead of manually writing YAML, learning query syntax, and iterating through trial-and-error testing, you collaborate with your AI to rapidly develop detections that work for your specific environment.
Use Cursor for IDE-based rule development or Claude Code for terminal-based workflows. Both integrate Scanner MCP to test rules against your actual data without leaving your development environment.
Learn more about Detection Engineering →
Example: Building a Privilege Escalation Detection
You want to catch attackers probing for privilege escalation vulnerabilities:
"I need to detect suspicious IAM activity in AWS. Specifically, catch when a user performs multiple failed IAM policy modification attempts (this suggests an attacker is probing for vulnerabilities). Flag users with 3+ failures in 1 hour. Exclude service accounts like terraform and ci-pipeline."
Your AI immediately generates this production-ready Scanner detection rule:
# schema: https://scanner.dev/schema/scanner-detection-rule.v1.json
name: "Excessive IAM Policy Modification Failures"
enabled: true
description: |
Detects suspicious IAM activity where a user performs multiple failed
attempts to modify IAM policies. This pattern suggests permission probing
or an attacker testing access controls.
References:
* https://attack.mitre.org/techniques/T1548/004/
severity: High
query_text: |
%ingest.source_type="aws:cloudtrail"
eventSource="iam.amazonaws.com"
eventName=(PutRolePolicy AttachRolePolicy)
errorCode=*
NOT userIdentity.userName=(terraform ci-pipeline automation-user)
| stats
count() as failed_attempts,
min(timestamp) as firstTime,
max(timestamp) as lastTime
by userIdentity.userName, eventName
| where failed_attempts >= 3
tags:
- techniques.ta0005.privilege_escalation
time_range_s: 3600
run_frequency_s: 300
alert_template:
info:
- label: User
value: "{{userIdentity.userName}}"
- label: Event Type
value: "{{eventName}}"
- label: Failed Attempts
value: "{{failed_attempts}}"
- label: Time Window
value: "{{firstTime}} to {{lastTime}}"
tests:
- name: Alert triggers on 3+ failed policy modifications
now_timestamp: "2024-08-21T00:10:00.000Z"
dataset_inline: |
{"timestamp":"2024-08-21T00:05:00.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"PutRolePolicy","userIdentity":{"userName":"attacker"},"errorCode":"UnauthorizedOperation"}
{"timestamp":"2024-08-21T00:05:30.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"AttachRolePolicy","userIdentity":{"userName":"attacker"},"errorCode":"AccessDenied"}
{"timestamp":"2024-08-21T00:06:00.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"PutRolePolicy","userIdentity":{"userName":"attacker"},"errorCode":"InvalidParameterException"}
expected_detection_result: true
- name: No alert for service accounts
now_timestamp: "2024-08-21T00:10:00.000Z"
dataset_inline: |
{"timestamp":"2024-08-21T00:05:00.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"PutRolePolicy","userIdentity":{"userName":"terraform"},"errorCode":"AccessDenied"}
{"timestamp":"2024-08-21T00:05:30.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"PutRolePolicy","userIdentity":{"userName":"terraform"},"errorCode":"AccessDenied"}
{"timestamp":"2024-08-21T00:06:00.000Z","%ingest.source_type":"aws:cloudtrail","eventSource":"iam.amazonaws.com","eventName":"AttachRolePolicy","userIdentity":{"userName":"terraform"},"errorCode":"AccessDenied"}
expected_detection_result: falseThen it tests against your last 30 days of data, finds 47 matches (mostly dev team false positives), you refine with "Too many false positives from the dev team," and it iterates to tune thresholds and exclusions. What would take hours of manual YAML writing takes minutes of conversation.
Your AI can also migrate rules from other platforms (Splunk, Datadog, Elastic), analyze your detection coverage against MITRE ATT&CK to identify gaps, and validate that new detections work against your actual data before deployment.
3. Autonomous Workflows
Autonomous workflows are AI agents that run continuously, investigating threats, triaging alerts, and orchestrating security operations 24/7 without human intervention.
Built with the Claude Agent SDK, these agents execute complex investigations automatically: they query Scanner for context, correlate findings across data sources, create tickets, notify teams, and maintain audit trails (all in seconds).
Learn more about Autonomous Workflows →
Example: End-to-End Autonomous Response
A high-severity alert fires at 2 AM. No analyst is online. Here's an agent built with the Claude Agent SDK that orchestrates the entire response workflow:
#!/usr/bin/env python3
import asyncio
import os
from datetime import datetime
from dotenv import load_dotenv
from rich import print as rprint
from claude_agent_sdk import query, ClaudeAgentOptions
async def autonomous_response_agent(alert_id: str):
"""
Automatically respond to security alerts:
1. Investigate with Scanner
2. Enrich with VirusTotal threat intel
3. Create Linear ticket
4. Post to Slack
"""
load_dotenv()
options = ClaudeAgentOptions(
model="claude-sonnet-4-5-20250929",
allowed_tools=[
"mcp__scanner__get_scanner_context",
"mcp__scanner__execute_query",
"mcp__scanner__fetch_query_results",
"mcp__virustotal__search",
"mcp__virustotal__get_ip_report",
"mcp__linear__create_issue",
"mcp__slack__send_message",
],
mcp_servers={
"scanner": {
"type": "http",
"url": os.environ.get("SCANNER_MCP_URL"),
"headers": {
"Authorization": f"Bearer {os.environ.get('SCANNER_MCP_API_KEY')}"
}
},
"virustotal": {
"command": "npx",
"args": ["@burtthecoder/mcp-virustotal"],
"env": {"VIRUSTOTAL_API_KEY": os.environ.get("VIRUSTOTAL_API_KEY")}
},
"linear": {
"command": "npx",
"args": ["-y", "mcp-remote", "https://mcp.linear.app/sse"],
},
"slack": {
"command": "docker",
"args": ["run", "-i", "--rm", "-e", "SLACK_BOT_TOKEN",
"-e", "SLACK_TEAM_ID", "mcp/slack"],
"env": {
"SLACK_BOT_TOKEN": os.environ.get("SLACK_BOT_TOKEN"),
"SLACK_TEAM_ID": os.environ.get("SLACK_TEAM_ID"),
}
}
}
)
prompt = f"""
I'm receiving a security alert (ID: {alert_id}) and need you to execute
a full response workflow.
Please:
1. **Investigate in Scanner**: Query for alert details, related activity
from user/IP in last 24 hours, severity assessment
2. **Gather Threat Intelligence**: For any IPs/domains/hashes involved,
search VirusTotal for reputation and malware information
3. **Create Response Ticket**: Use Linear to create incident ticket with:
- Title: Concise description
- Description: Full investigation summary with findings
- Priority: Set based on severity (High/Medium/Low)
4. **Notify Team**: Post to Slack with alert summary, severity,
key findings, and link to Linear ticket
5. **Classification**: Classify as Confirmed Threat, Suspicious,
or Likely False Positive with confidence level
"""
rprint(f"[{datetime.now().isoformat()}] Starting autonomous response...")
async for message in query(prompt=prompt, options=options):
rprint(message)
rprint(f"[{datetime.now().isoformat()}] Response workflow complete.")
if __name__ == "__main__":
asyncio.run(autonomous_response_agent(
alert_id="a3f2c8b1-5d4e-4a9c-8f7e-2b1a6c9d4e5f"
))By the time your team comes online, the incident is documented, triaged, and ready for response: ticket created, team notified, threat intel gathered. No manual work required.
Scanner Customers Are Already Building
Since launching Scanner MCP in beta, security teams have started integrating it into their production workflows.
Teams are building agents that triage alerts, run scheduled threat hunts, and automatically investigate IOCs, automating workflows that previously required manual analyst work.
Getting Started
Scanner MCP is available now for all Scanner customers. Setup takes minutes:
- Get your Scanner API key from Settings > API Keys
- Configure your tool (Claude Desktop, Claude Code, Cursor, or Claude Agent SDK)
- Start investigating with natural language queries against your security data
See our Getting Started guide for detailed setup instructions.
For customers building autonomous workflows, we've published example agents and best practices in our Autonomous Workflows documentation.
What's Next
This is just the beginning. We're seeing security teams reimagine how security operations work when AI agents have direct access to comprehensive security data without performance or cost barriers.
The future of security operations isn't replacing analysts with AI. It's giving analysts AI-powered tools that scale their expertise. Interactive investigations for critical incidents requiring judgment. Detection engineering to prevent the same attacks from recurring. Autonomous workflows to handle routine operations 24/7.
If you're a Scanner customer, Scanner MCP is available in your environment today. If you're evaluating security data platforms and want to see what AI-native security operations look like, reach out to our team.
Scanner MCP is available now in beta. For setup instructions, documentation, and examples, visit docs.scanner.dev/mcp-and-ai-secops.

