Run Hundreds of Detection Rules at Scale
Streaming detection engine runs hundreds of rules simultaneously without scanning the same data repeatedly. Start with 400+ out-of-the-box rules or write custom detections as code.

400+
20+
<100ms
<5min
From zero to detection coverage in minutes
Import pre-built rules, test safely, route alerts, and investigate fast.
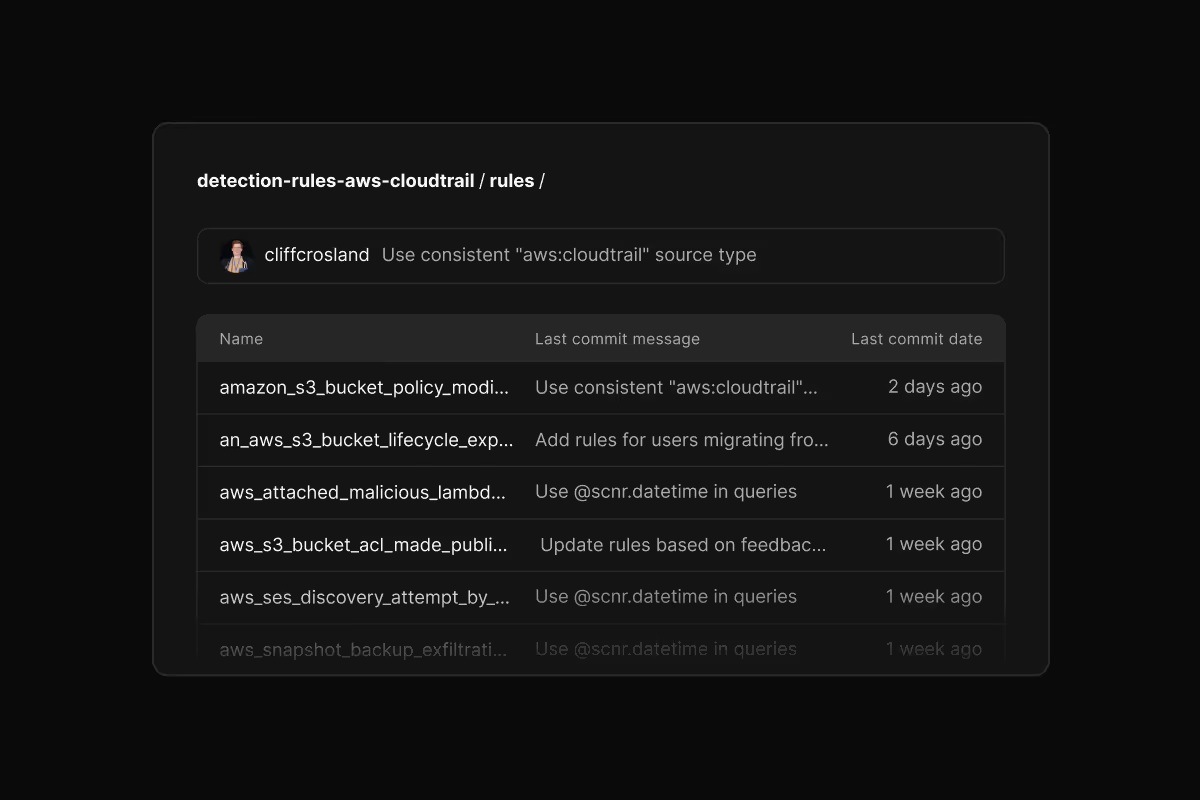
Import pre-built detection rules
Start with 400+ out-of-the-box detection rules covering 20+ log sources. Connect a GitHub repository, select which rules to sync, and Scanner automatically keeps them updated as the community improves them.
Covers AWS, GCP, Azure, Okta, GitHub, M365, Slack, Snowflake, and more. Each rule includes descriptions, severity levels, and recommended alert routing.
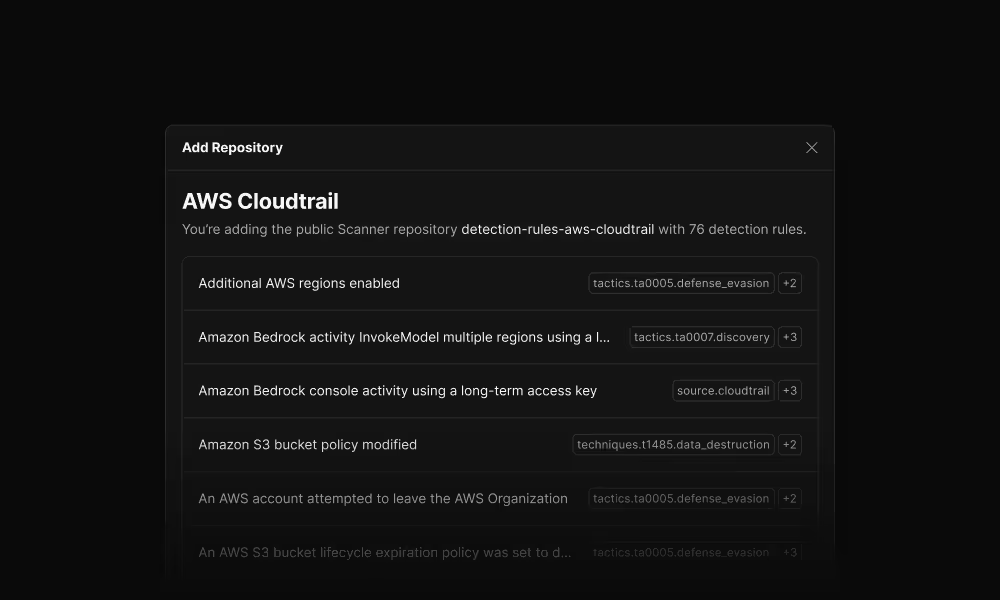
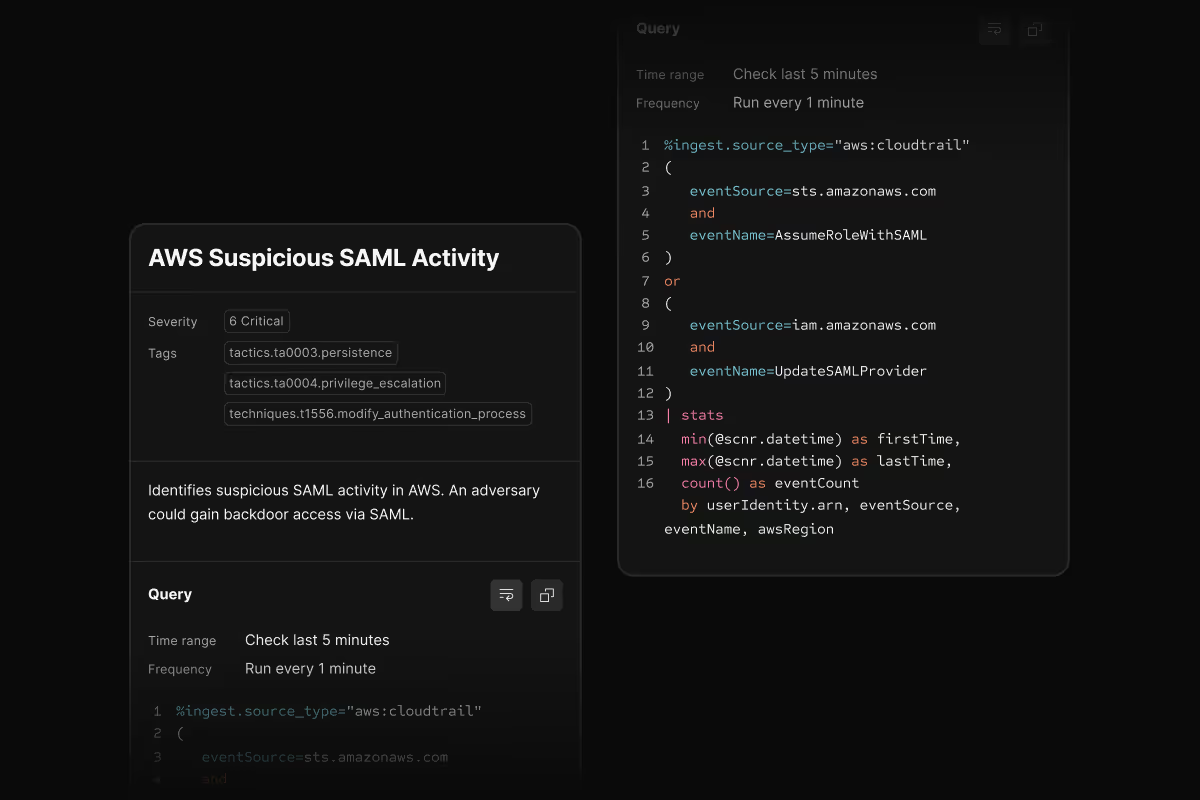
Write custom rules your way
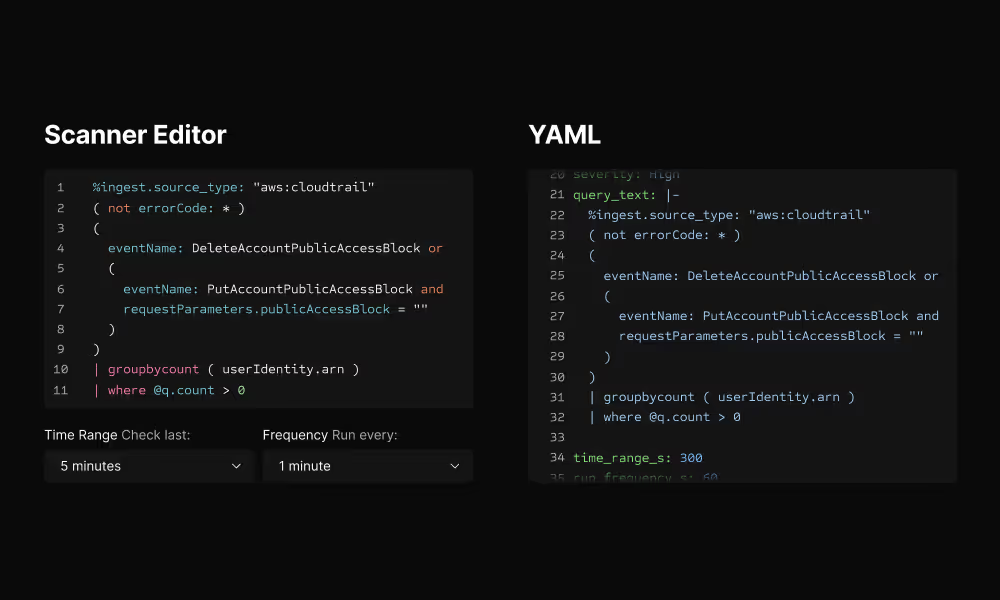
Create rules from scratch in the Scanner UI, duplicate and modify existing OOTB rules, or write rules in YAML and version control them in GitHub. Use the same query language you already know from search.
GitHub-based rules sync automatically. Test detection logic in your CI/CD pipeline and require code review before deploying to production.
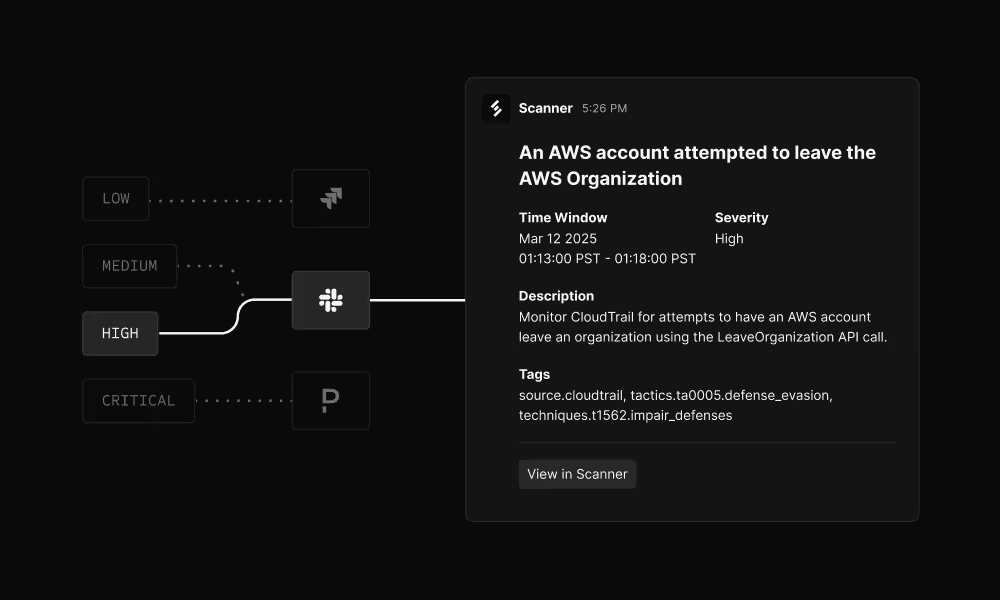
Route alerts where your team works
Send critical alerts to PagerDuty for immediate on-call response. Medium-severity alerts go to Slack for team awareness. Low-priority alerts go to your ticketing system. Configure routing by severity level.
Alerts include context about what happened and link directly to investigation. Integrate with Slack, Microsoft Teams, PagerDuty, Jira, or any system via webhooks.
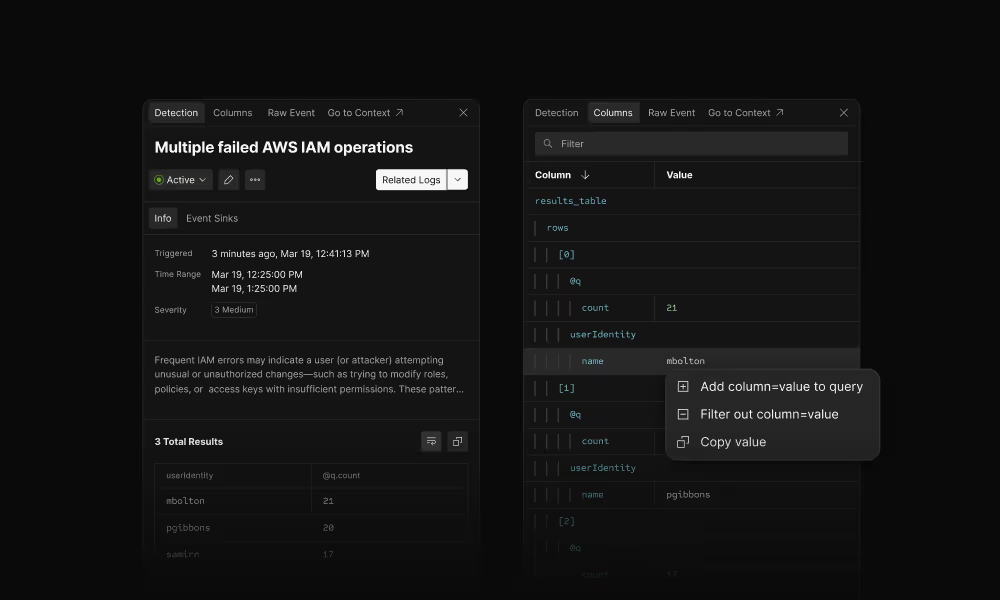
Investigate alerts efficiently
Click an alert and immediately see what matters: the event data, who was involved, and what happened. No digging through rule metadata or running manual queries to understand the incident.
Click any field value to investigate further—see all related activity from that user or IP, filter to similar events, or jump straight to raw logs. Investigation happens in the same tool where the alert fired.
Built for fast-moving security teams
Everything you need to detect, investigate, and respond to threats.
Version control
Manage detection rules in GitHub alongside your code. Review changes, test in CI/CD, and deploy with confidence.
Write rules your way
Use the same query language you already know from search. Complex logic, time-range correlations, cross-log queries—it all works.

Alert to investigation in one click
Every alert links directly to investigation. See what triggered, pivot to related activity, and drill into raw logs without switching tools.
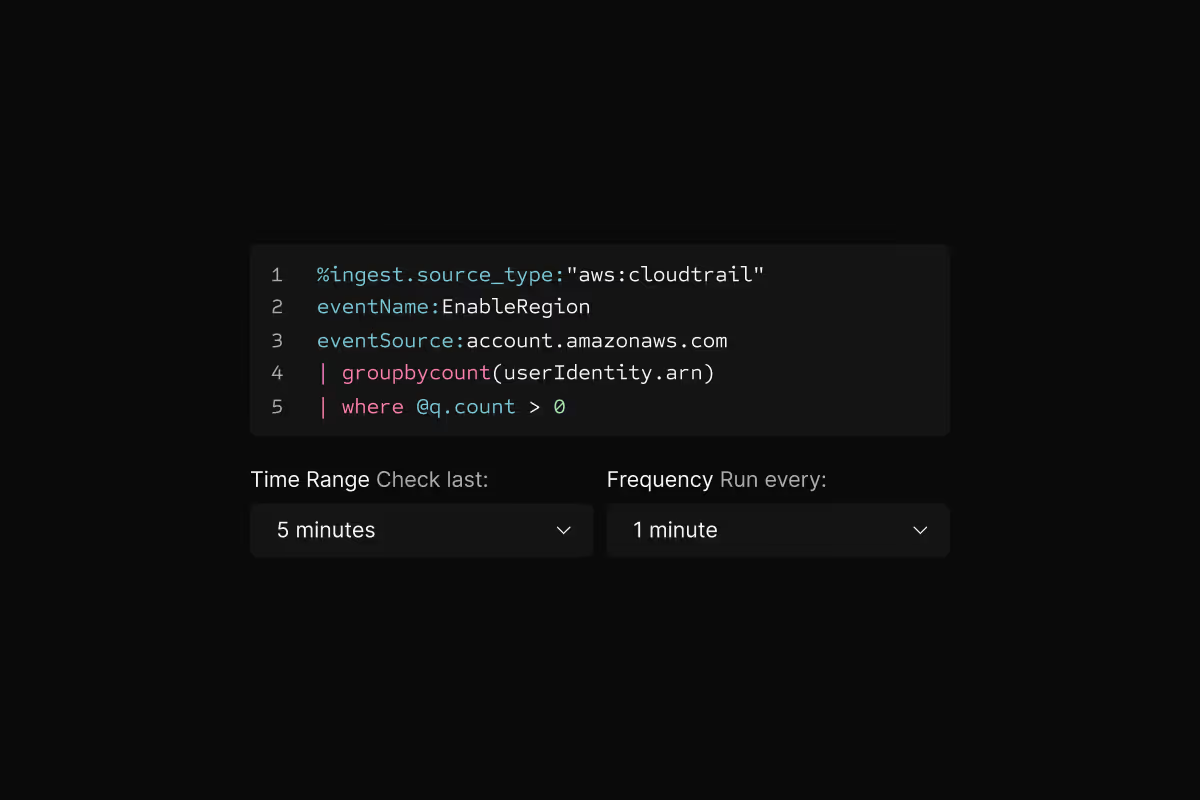
Run rules as often as needed
Check critical detections every minute or run compliance checks daily. Each rule runs independently at its own frequency.
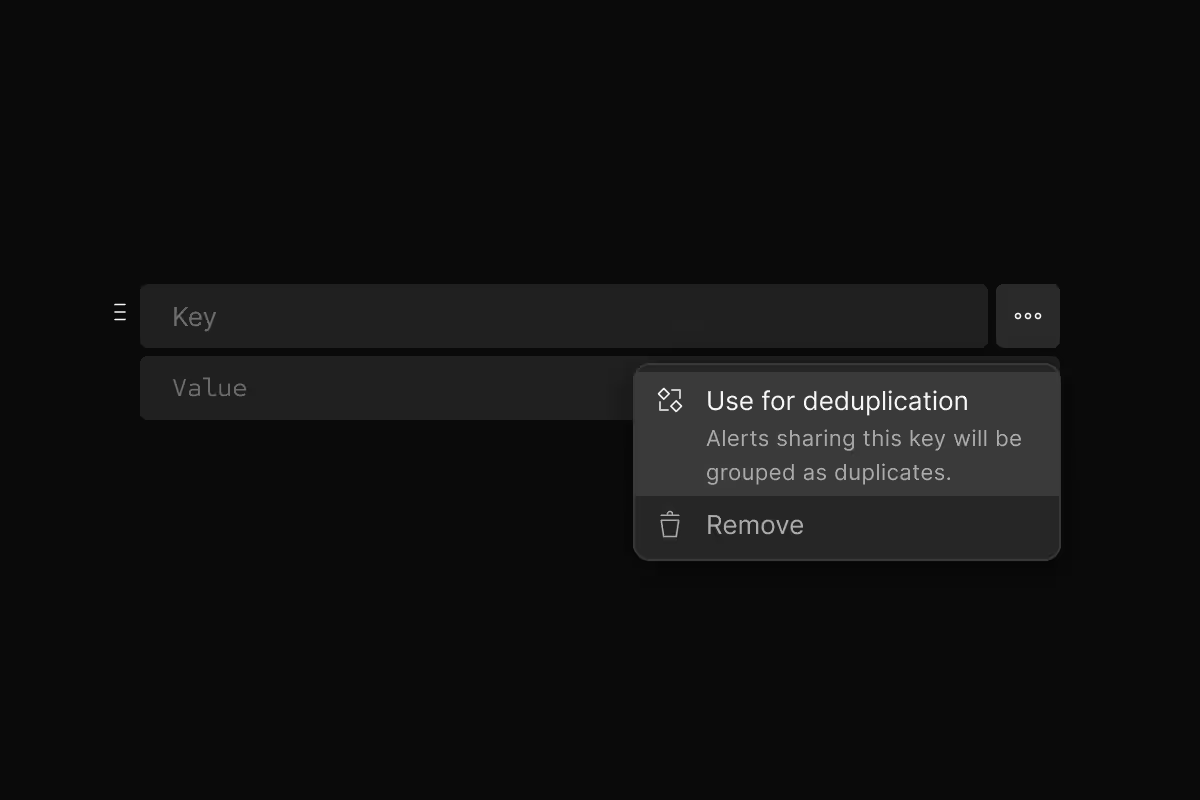
Stop alert fatigue
Automatically group repeat alerts into single notifications. No more being woken up 50 times for the same issue.
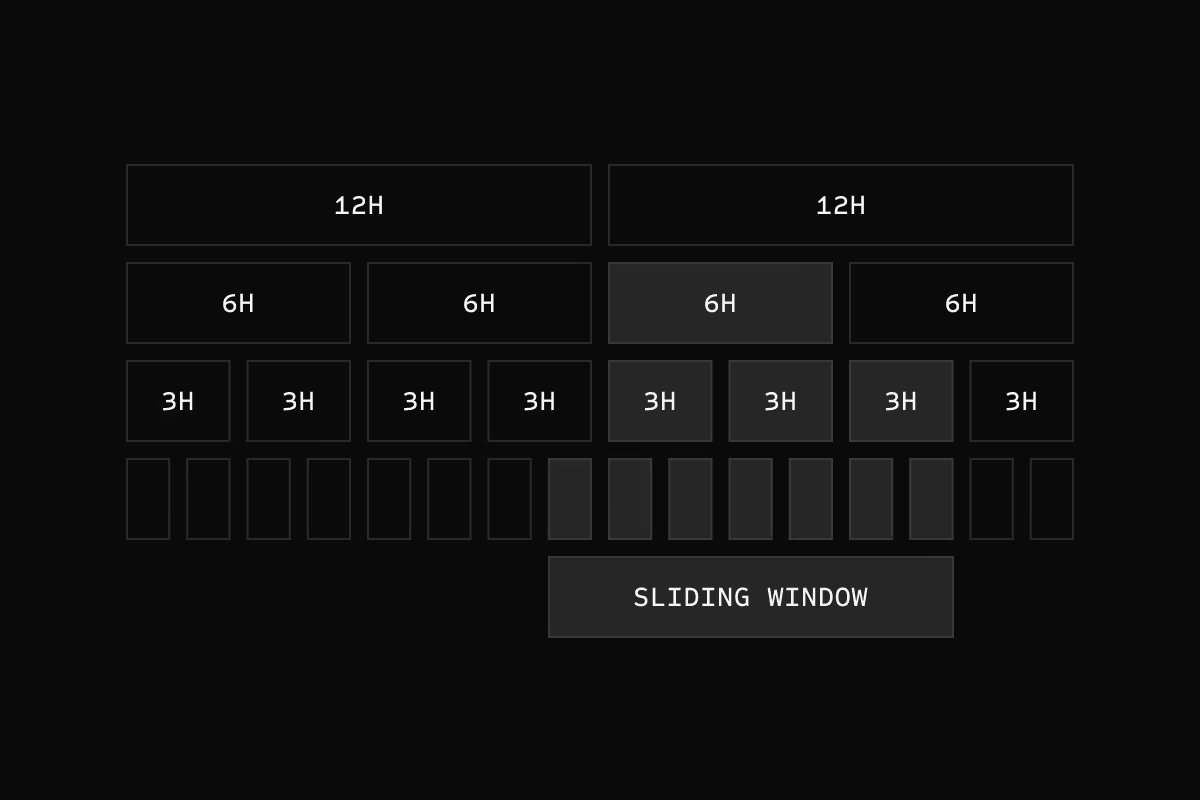
Never miss delayed logs
Handles logs that arrive late or out of order. Automatically re-evaluates and alerts if delayed data crosses thresholds.
Scanner unlocks the power of your security data
A cloud-native security data lake that never slows down, never drops data, and gives you complete control.
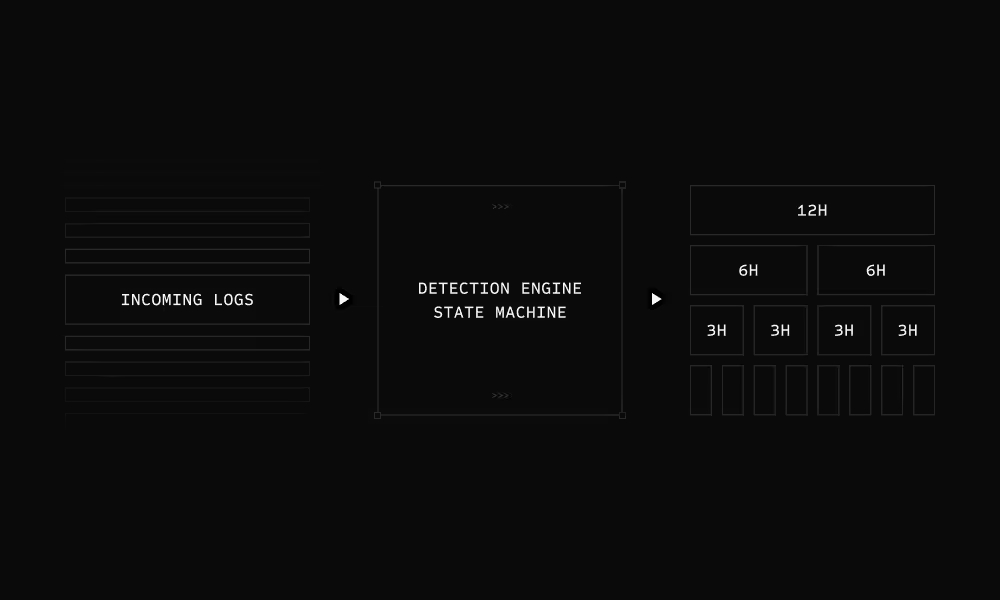
Streaming Detection Engine
Detection rules run during indexing. Logs are processed against all rules simultaneously. Matching logs execute up to their first aggregation, and results are cached in a time-based rollup tree in S3.
Detection rules run during indexing. Logs are processed against all rules simultaneously. Matching logs execute up to their first aggregation, and results are cached in a time-based rollup tree in S3.
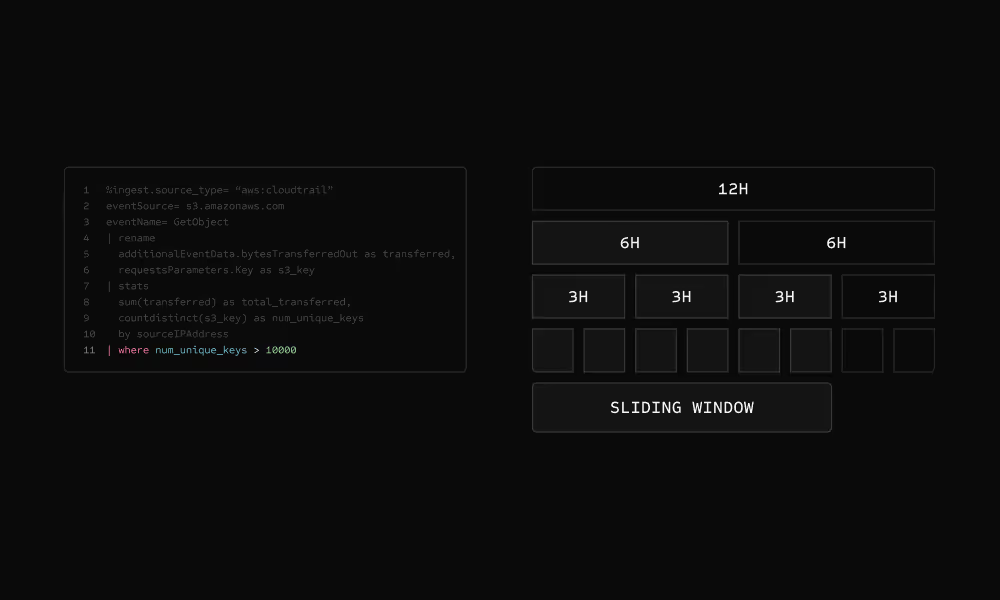
Query the cache, not raw logs
Detection workers query the rollup tree—a segment tree data structure optimized for time-range queries. Checking a 24-hour window reads only the minimal nodes needed. Queries complete in under 100ms.
500 rules checking every minute = 3.6TB queried daily vs 7.2PB with scheduled queries. ~2,000x more efficient.
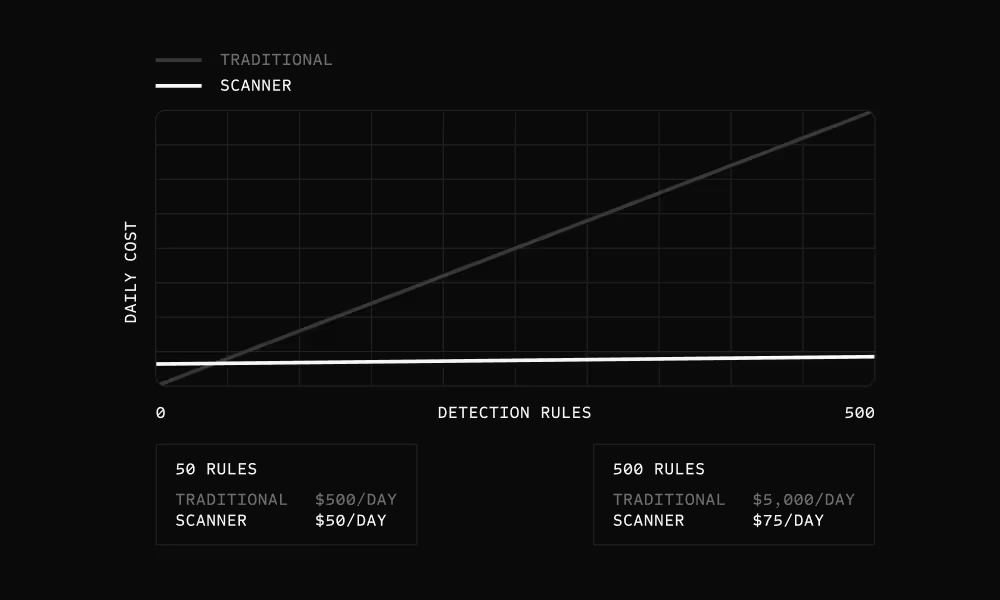
Cost scales with volume, not rules
All rules share the same indexing pass. Adding detection rules doesn't require re-scanning logs. Cost scales with log volume, not rule count.
50 rules: Traditional $500/day, Scanner $50/day. 500 rules: Traditional $5,000/day, Scanner $75/day.
FAQ
Yes. All detection rules are open-source YAML files in GitHub. You can fork the repositories, modify rules for your environment, and sync your customized version to Scanner. You can also enable/disable individual rules and adjust parameters like thresholds, time windows, and severity levels.
Detection rules can check as frequently as every 1 minute. The actual detection check (querying the rollup tree cache) typically completes in under 100 milliseconds, even for queries looking back 24 hours. Configure check frequency per rule: 1 min, 5 min, 15 min, 1 hour, 6 hours, or 1 day.
Alerts can be routed to Slack, Microsoft Teams, PagerDuty, or any webhook/SOAR platform. You configure routing by severity - for example, send critical alerts to PagerDuty, medium to Slack, and low to a ticket system. All detection events are also stored in the _detections index for investigation.
The marginal cost of adding rules is minimal because all rules share the same indexing infrastructure. New rules automatically process incoming logs and build their rollup tree caches. Detection workers scale separately, so adding rules doesn't impact indexing performance. There's no maximum number of detection rules.
Currently, detection rules can look back up to 24 hours. This covers most real-time detection use cases. For longer-term anomaly detection or baseline analysis, you can run ad-hoc queries on historical data and use the results to tune detection thresholds.
Start Detecting Threats in Hours, Not Months
See how Scanner's streaming detection engine can give you comprehensive coverage without the traditional cost and complexity.
